The Glen Park public library in San Francisco is usually a quiet, calm place. No more so than the science-fiction section, where nerds congregate to read their emails on the free Wi-Fi. On Tuesday that tranquility was rudely interrupted when half a dozen FBI agents descended on the startled sci-fi guys and surrounded, then arrested, a 29-year-old man quietly working on his laptop.
The FBI claims the man it detained, Ross William Ulbricht, is an international drug smuggler known online by the alias Dread Pirate Roberts. They say he is responsible for setting up and running Silk Road, an ingenious underground online illicit marketplace known as "the Amazon.com of illegal drugs."
Ulbricht has been hit with a number of serious charges: narcotics trafficking conspiracy (including more than a kilogram of heroin, five kilograms of cocaine, 10 grams of LSD and 500 grams of methamphetamine); computer hacking conspiracy; and money laundering conspiracy. As soon as Ulbricht was lifted, Silk Road was promptly shut down, the result of a nearly two-year investigation by the FBI — headed by agent Christopher Tarbell, the Eliot Ness of online crime, and a tech-savvy investigator known simply as Agent-1 — that involved moles who infiltrated the market, hackers, thousands of counterfeit IDs, and an attempted assassination.
"The Silk Road website has served as a sprawling black-market bazaar where illegal drugs and other illicit goods and services have been regularly bought and sold by the site's users," said Tarbell. "Based on my training and experience, Silk Road has emerged as the most sophisticated and extensive criminal marketplace on the Internet today. The site has sought to make conducting illegal transactions on the Internet as easy and frictionless as shopping online at mainstream e-commerce websites."
Silk Road could only be accessed through The Onion Router, a network designed to protect online anonymity and make it extremely difficult to physically locate computers accessing certain websites. Silk Road transactions were paid in Bitcoins, an electronic currency designed to be as anonymous and untraceable as cash.
The challenge wasn't in determining that Silk Road was conducting thousands of illegal transactions – undercover FBI agents had been buying drugs and employing hackers since November 2011. The challenge was determining the true identity of Dread Pirate Roberts, an arch-criminal masterminding the site whose name was lifted from William Goldman's book and film The Princess Bride.
While Tarbell led the investigation, Agent-1 had the hacking skills necessary to penetrate Roberts's domain. The identity of Agent-1 is not quite what it seems. He may not simply be a Fed agent with computer skills.
Some believe Agent-1 is actually Hector Xavier Monsegur, a.k.a. Sabu, a leading figure in the hacktivist collective Anonymous and member of an elite group of hackers known as LulzSec. Tarbell arrested Monsegur in June 2011 and, like a Cold War spy, turned him, using him to track down other members of LulzSec. The FBI has continued to postpone Monsegur's trial, leading many to conclude that he continues to work as an informant.
Agent-1 and Tarbell started their investigation with an exhaustive search of the Internet, including the Surface Web and Deep Web, for clues about their cunning prey, the ingenious amoral hacker running Silk Road.
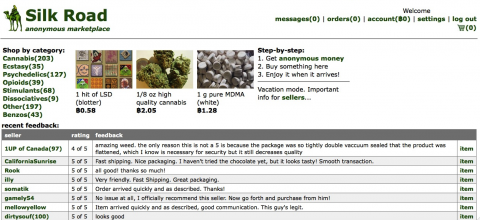
The first mention of Silk Road that Agent-1 could find was a January 27, 2011 post titled "anonymous market online" on a discussion forum catering to those whose drug of choice is psychedelic mushrooms. The user who posted the query was identified simply as "altoid," and the post linked to a Wordpress blog created just four days earlier. Agent-1 then found a second post made just two days later on a Bitcoin discussion forum. The unidentified user of that post was also altoid.
The timing of the posts and the fact that both ended with "Let me know what you guys think," led Tarbell to conclude that altoid was someone drumming up business for Silk Road.
Altoid posted to the Bitcoin forum again about eight months later, this time looking to hire an "IT pro" for a "venture backed Bitcoin startup company." The post instructed interested parties to email rossulbricht@gmail.com. It was a breakthrough for Tarbell and Agent-1. They now had a name.
The email address was linked to a Google+ account – Google's social network – and included a photograph of Ulbricht. This matched a "Ross Ulbricht" LinkedIn profile picture, which gave Tarbell the first personal details of his main suspect.
The Fed agents discovered that Ulbricht graduated from the University of Texas in 2006 with a bachelor of science in physics and went to graduate school at the University of Pennsylvania School of Materials Science and Engineering from 2006 to 2010. On the profile, Ulbricht said his personal goals changed after grad school, shifting to "creating an economic stimulation to give people a firsthand experience of what it would be like to live in a world without the systemic use of force."
Then came a second breakthrough. Tarbell noticed that several of the links Ulbricht shared on his Google+ page matched websites and YouTube videos regularly cited by Roberts.
Tarbell obtained logs from Google to determine that the Gmail account was regularly accessed by a Comcast IP address. He tracked this virtual address to a building on Hickory Street in San Francisco, and discovered it belonged to a close friend of Ulbricht. According to a YouTube video posted by Ulbricht and his pal, Ulbricht was staying with the friend when he moved to live in San Francisco in September 2012. Ulbricht's house move coincided with references by Roberts to the Pacific time zone.
Roberts ran Silk Road by accessing the site with a virtual private network (VPN), so that only a specific IP address could access it. The investigation stalled for a while when it was discovered the contents of this VPN server had been erased. But then came a stroke of luck. Tarbell and Agent-1 found a single record of the last IP address used to access the VPN server and traced it to an Internet café on Laguna Street, less than 500 feet from the address on Hickory Street where Ulbricht was staying.
"Based on my training and experience, this evidence places the administrator of Silk Road, that is, DPR, in the same approximate geographic location, on the same day, as Ulbricht," Tarbell wrote in the complaint.
Meanwhile, oblivious that Federal agents were now tracking his every move, Roberts came under heat from an unlikely source. A customer on Silk Road with the username "FriendlyChemist" threatened to reveal a long list of real names and addresses of Silk Road vendors and customers unless Roberts paid $500,000. One of the world's most successful drug dealers was being blackmailed.
Roberts pondered what to do. With his multimillion-dollar business at risk, he contacted someone using the username "redandwhite" and agreed to pay him $150,000, in Bitcoins, to kill FriendlyChemist.
Redandwhite told Roberts he had made the hit and that he would no longer hear from FriendlyChemist. He showed him photographs of FriendlyChemist's corpse as proof. If a killing did take place, there is no official record of it. Canadian police say they do not have any record of a homicide that matches what little is known of the victim and the purported assassin.
Tarbell and Agent-1 eavesdropped on the mercenary relationship between Roberts and redandwhite, and on June 1, 2013, came the third breakthrough in the case. Roberts contacted redandwhite to ask about buying counterfeit IDs so he could rent more servers to increase the capacity and reach of Silk Road.
On July 10, 2013, U.S. Customs and Border Protection intercepted a package from Canada with nine counterfeit IDs. The information on each ID was different, yet all were addressed to the same location on 15th Street in San Francisco, and each featured an image of Ulbricht. When approached by Homeland Security, Ulbricht denied all knowledge of Silk Road and refused to answer questions about the IDs, though officers were able to establish an important fact about his behavior: He always paid his rent with cash. When Homeland Security questioned Ulbricht's roommates, they said they only knew him as "Josh" and that he spent most of his time sitting alone in his room, working on his computer.
The final piece of the puzzle fell into place when Tarbel and Agent-1 found the record of an account created on Stack Overflow, a question-and-answer service used by programmers, with the user name "Ross Ulbricht" registered to the Ross Ulbricht Gmail account. The user name was later changed to "frosty," but the account holder posted questions about software code that coincided with code used in the construction of Silk Road's website.
The Internet café Ulbricht used to inhabit to throw investigators off the scent was right next door to the Glen Park public library. When Ulbricht was arrested, police also seized about 26,000 Bitcoins belonging to him, worth about $3.6 million. His arrest and the subsequent closure of Silk Road caused the value of Bitcoin to drop 20 percent, thought it has since recovered. The future of unregulated virtual online currencies has been put in doubt by such landmark criminal cases.
Ulbricht, through his lawyers, has denied all charges and has declined to comment further on one of the most important cybercrime cases ever brought. Friends of Ulbricht have said they cannot believe he could have had anything to do with such a heinous crime.
If convicted, Ulbricht could face spending a substantial portion of his life in prison. But even the stiffest sentence won't stop the spread of underground online black markets. Rival websites on the Deep Web, like Sheep and Black Market Reloaded, are experiencing surges in users since Silk Road was shut down. And Ulbricht's colleagues have already let it be known that Silk Road 2.0 is already constructed and ready to launch.



















